Single sign-On | FAQ
How does SSO differ from MFA?
SSO is a login method enabling users to access multiple resources with a single username/password authentication. Multi-factor authentication (MFA) requires more than one element or factor to authenticate a user’s identify before allowing a login to proceed. For example, a username plus a verification code or a security token. While MFA can be used for a single application, it is frequently combined with SSO.
A Salesforce email reminds me to update my SSO certificate. What do I do?
Salesforce Dot Com (SFDC) certificates expire every year and need to be updated within the org. If you receive a SFDC Expired Certificate Notification resolution instructions are available on the Sage People Community.
Ensure the updated certificate is uploaded to the single sign on integration. This is typically handled by your IT support team.
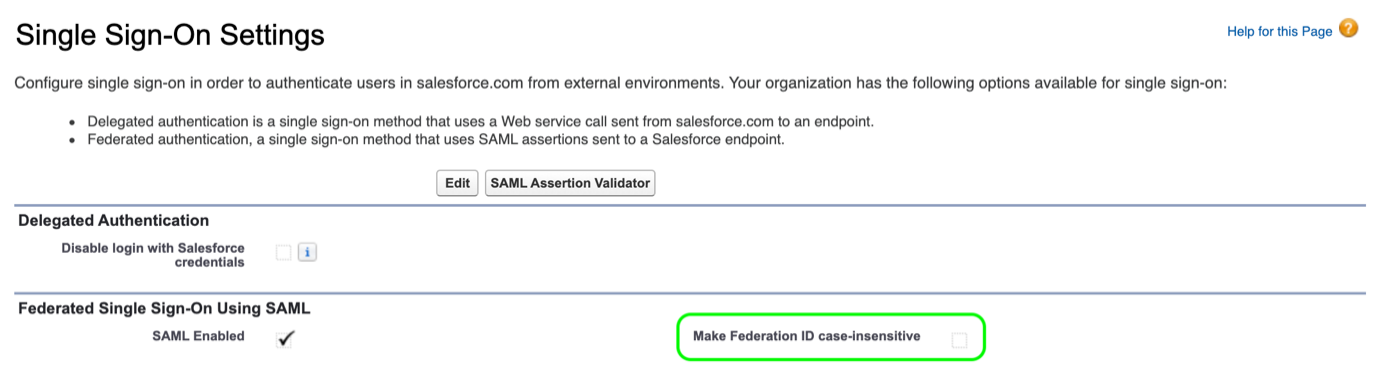
Can I turn off case sensitivity for SSO logins?
Yes:
- Go to Setup > Single Sign-On Settings
- Select Edit
- Select the checkbox for Make Federation ID case insensitive
- Select Save.
A team member cannot login using SSO. How do I fix this?
The fix depends on the error message received by the team member when they attempt to login:
-
If the error references either Sage People or Salesforce, the issue is most likely to be an incorrect Federation Id.
-
If the error message does not reference Sage People or Salesforce, the cause is a local IT issue. It is most likely the user has not been provisioned in the SSO app in the cloud service. Refer to your organization’s IT support team for resolution.
-
If one or more but not all team members cannot login to Sage People using single sign-on, and they are receiving a Sage People or Salesforce error message, follow these steps:
-
Go to Setup > Single Sign-On Settings and select SAML Assertion Validator.
-
There may be several errors on this page. Scroll to the bottom of the page to find the error:
Unable to map the subject to a Salesforce.com user. The identifier used in the SAML request from your SSO provider, usually referred to as a UPN (User Principal Name), does not match the identifier, usually the Federation Id, of the user trying to login.
NoteThe team member’s User record does not display an error because Salesforce cannot identify which user is trying to login.
-
You can:
-
Amend the UPN for the team member in the SSO service to match the value used in Salesforce. Refer to your organization’s IT support team for resolution.
-
Modify the Federation Id (or Username, if used instead) to match the value in the SAML Assertion Validator above, from within the User record.
Ensure the values match and remember by default Salesforce Federation Ids are case sensitive. You switch off case sensitivity by enabling the Make Federation ID case-insensitive option in Setup > Single Sign-On.
-
-
No one can login to my Sage People org using SSO. What do I do?
This problem is most commonly caused by a certificate mismatch between the SSO certificate in your SSO service and the SAML Single Sign-On Settings in your org. Your IT team typically maintains the certification of the SSO service, but with system administrator access to your org you can update the SAML settings in the org:
-
Login to the org using the login.salesforce.com page and your Salesforce username and password.
-
Go to Setup and in Quick Find enter Sign-On Settings.
-
On the Single Sign-On Settings page select SAML Assertion Validator.
-
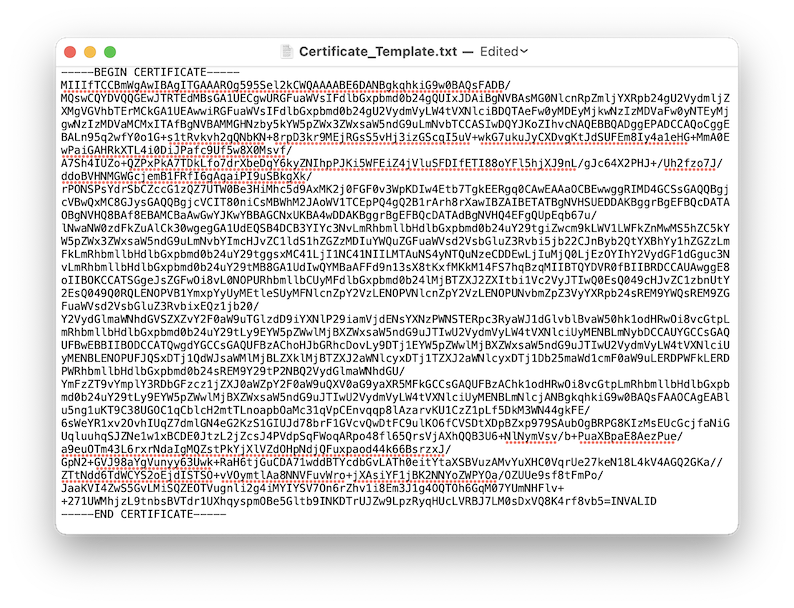
This page typically displays several errors. Copy the value from the SAML Response field at the bottom. This is a long text string.
-
Go to https://www.samltool.com/decode.php and paste the SAML Response into Deflated and Encoded XML.
-
Select Decode and Inflate XML.
-
In Deflated XML the page displays a long string of characters between <ds:X509Cert> and </ds:X509Cert>.
-
Save the file with a name you can easily identify and rename the extension to .cer
-
Go back to the org and navigate to the SSO service presenting the problem.
-
Select Edit and then Choose File next to Identity Provider Certificate.
-
Upload the file you created above and select Save.
-
Return to SAML Assertion Validator and ensure the errors are no longer be present.
All users should now be able to login using SSO.
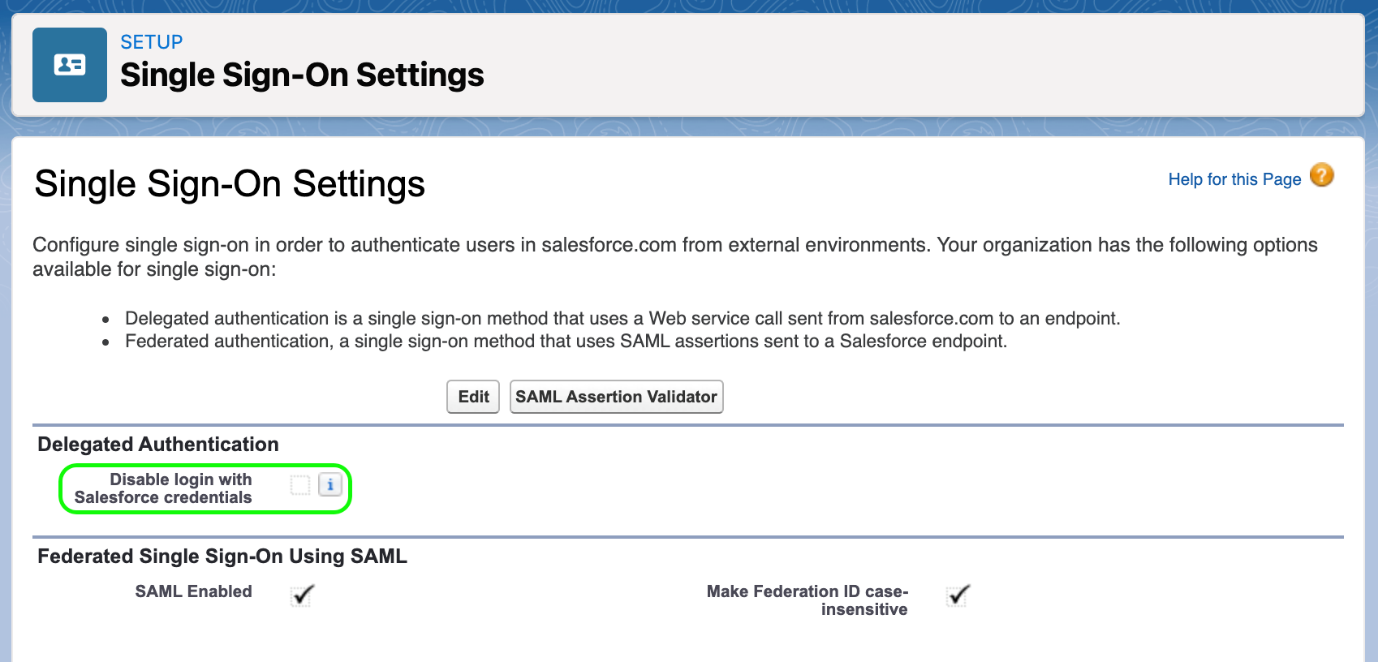
I can still login to my org with Salesforce credentials. Can I disable this?
Sage People recommends retaining a working Salesforce username and password for:
-
At least one system administrator to retain system access if your single sign-on service fails.
-
Pre-boarders who do not yet qualify for full access through SSO.
-
API access to your org.
To control which users can use SSO and which retain Salesforce login access, use a setting in Profiles or Permission Sets in combination with a setting on the Single Sign-On Settings page:
-
Go to Setup and in Quick Find enter Sign-On Settings.
-
In the Delegated Authentication section select Disable login with Salesforce credentials:
When selected, this option makes another SSO related item available to the profiles and permission sets for your org:
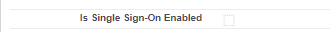
-
In the profiles or permission sets assigned to users who require Salesforce login access, ensure Is Single Sign-On Enabled is unchecked.
-
In the profiles or permission sets assigned to users who require SSO access and not Salesforce login access, ensure Is Single Sign-On Enabled is checked.
Does Federation ID automatically synchronize from Team Member to User?
Yes. There is no need to create a separate flow to synchronize the Federation ID.